GIAC Certified Forensic Analyst Review
My experience pursuing the GCFA certification, including the challenges it presented and the study strategies that helped me succeed.
Cory Atkinson


Disclaimer
SANS courses are fantastic, and fantastically expensive. I was lucky enough to have my company pay for my courses. If you are just starting out, try to get into the SANS Cyber Academy (scholarship funded).
https://www.sans.org/cyber-academy#faqs
Introduction
The GIAC Certified Forensic Analyst exam was a beast — easily the most difficult certification I’ve taken to date (as of December 2025). The challenge wasn’t just the material itself (though that proved a monumental task). At the time, I was still early in my Windows forensics journey, juggling an ambitious workload, and balancing life as a father and husband. Even so, I managed to walk away with a 94%.
My approach to SANS exams hasn’t changed much over the years, but for this one I’ll break down the general content, how I studied, what the test experience was like, and whether I think the certification is worth pursuing.
For transparency, all of my SANS/GIAC experience has been with the Live version of the courses.
If you want to verify that I actually earned the certification, here’s the Credly link: https://www.credly.com/badges/5bc530e8-af77-4048-bc57-6dd93915f14f
Brief Overview of the Course
FOR508: Advanced Incident Response, Threat Hunting, and Digital Forensics is enormous in scope. I would not recommend this course to anyone who is brand new to cybersecurity — the sheer volume of material will overwhelm you quickly.
The course covers a wide range of topics, including:
Log sources and log parsing
Incident response tooling and workflows
Domain configuration and security considerations
Prefetch, Amcache, and other Windows artifact analysis
File system forensics
Memory acquisition and analysis
Triage image capture
NTFS artifiact analysis
Threat hunting methodology
And much more — truly too much to list in full
One of my takeaways was discovering the Eric Zimmerman tool suite. These tools have become part of my daily workflow, and I can’t imagine doing Windows forensics without them now.
Overall, the course is dense, fast‑paced, and packed with practical knowledge. It was a massive amount of information to absorb, but it fundamentally changed the way I approach DFIR. I’ll be writing a full, in‑depth review of the course soon.
Study Prep
Attend the SANS course.
If you don't have the books, and have not attended the course, I do not recommend taking the exam. Certifications are beneficial not due to the paper they give you, but because of the education it imparts.
Also if you get the chance, participate in the CTF. Its fun, don't take it too seriously and view it as a learning opportunity.
Schedule your exam
A firm date always helps me to lock in and focus.
Read your books.
Re-Read your books, while creating an index.
I loosely follow these guidelines https://tisiphone.net/2015/08/18/giac-testing/
My main practice is index anything I think is useful, obscure or that I will reference in the future.
I look at these books as future reference material and treat them as such. I continously come back to them, throughout my career.
While indexing make flash cards, I use Anki. Free on PC, onetime fee on phone.
Paper flash cards work as well.
Do the labs.
Take the practice test.
Review missed content.
Especially the labs, if you had trouble in any of the labs its time to get some serious reps in.
Do some endpoint forensic labs on CyberDefenders, Hack the Box or TryHackMe.
Take the last practice test.
Take the exam.
Brief Overview of the Exam
There’s only so much I can say here, but here’s what I can share.
The exam is challenging — more challenging than many expect. You’ll be tested on concepts that may seem obscure or easy to overlook during your studying, so don’t skip anything. Read the material, review it, and most importantly, practice it. The multiple‑choice section felt tough but fair. Personally, I always enjoy the CyberLive portions more; they’re hands‑on, engaging, and feel closer to real work. If you’re performing well on the practice exams, you’re likely in good shape — as long as you stay calm. I’ve consistently scored higher on the real exam than on the practice ones (78% and 88%), probably because I tend to focus better under pressure. Additional tip I took the exam remotely and my camera, which had worked for every previous exam, suddenly failed, and I had to scramble for a replacement. Lesson learned: always test your setup and the Guardian browser before exam day.
Is It Worth It?
Here’s how I evaluate any certification before recommending it:
Does it make me better at cybersecurity in a practical, applicable way?
Yes. Absolutely.
Does it move me toward my career goals?
Yes. I’m aiming for DFIR, threat hunting, or a similar role, and this course aligns perfectly.
Do I gain real knowledge, or just a piece of paper?
Knowledge — and a lot of it. The certification is just the byproduct.
Is the certification respected?
Yes. I’ve seen it listed in many job postings, which tells me HR and hiring managers recognize its value.
Verdict
If you’re not paying out of pocket, I strongly recommend taking both the course and the certification.
Before this class, my experience in DFIR, threat hunting, endpoint forensics, and log analysis was limited. Afterward, I felt like a practitioner. I’ve already applied what I learned to my organization: building an incident response program, began threat‑hunting, developing stronger IOCs, training others on triage image acquisition, and filling in knowledge gaps that had held me back. It even improved my performance in DFIR CTFs.
The deep dive into Windows internals alone made me a better analyst and more confident in my day‑to‑day decisions. I still revisit the FOR508 material regularly — it’s become one of my most valuable references and easily my favorite SANS course so far.
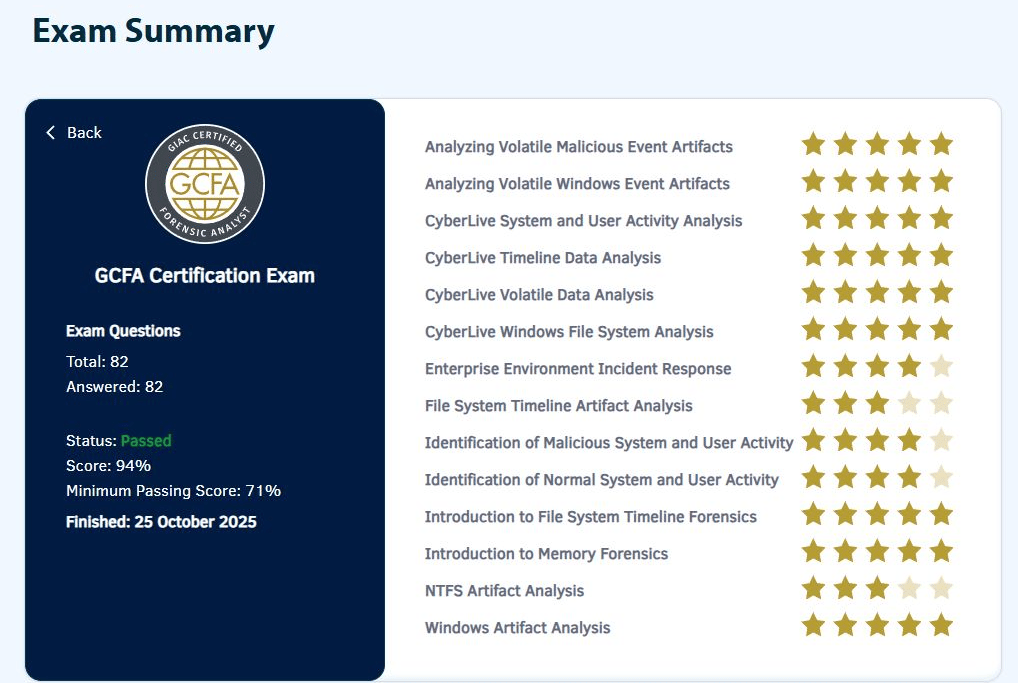
GIAC Exam Objectives (2025)
Analyzing Volatile Malicious Event Artifacts
Analyzing Volatile Windows Event Artifacts
Enterprise Environment Incident Response
File System Timeline Artifact Analysis
Identification of Malicious System and User Activity
Identification of Normal System and User Activity
Introduction to File System Timeline Forensics
Introduction to Memory Forensics
NTFS Artifact Analysis
Windows Artifact Analysis
